Petya cyberattack spreads to 65 countries
The path of Petya slowly swept across the globe Wednesday, infiltrating more major multinational businesses.
The ransomware attack spreading through computers in North America and Europe has now reached 65 countries, Microsoft said Wednesday morning. On Tuesday, cybsecurity experts said Petya hit six countries.
"We are definitely dealing with a very pervasive, large scale global ransomware attack," said Robert Anderson, the managing director of information security at Navigant Consulting who previously worked at the FBI investigating cyberattacks. "It's hitting multiple infrastructure targets and over the next few days I suspect it will hit more."
Members of Microsoft's security team said in a blog post more than 12,500 machines were hit in Ukraine alone. Microsoft believes the attack started with a company that makes tax accounting software.
The maker of the Windows operating system says its researchers have proof some of the infections started through the process used to update software from M.E. Doc, the Ukrainian developer.
"Given this new ransomware’s added lateral movement capabilities it only takes a single infected machine to affect a network," read an excerpt of Microsoft's post.
The ransomware is a newer "more sophisticated" version of the Petya virus, Microsoft confirms. It also urges computer users to update their devices. This has led to security experts divided on what to call the ransomware — some call it "NotPetya" because of differences from the original — and others to dub it "Goldeneye," after another recent strain of Petya.
Several big companies were hit by the Petya attack, which started spreading Tuesday, including Russian oil company Rosneft, shipping firm A.P. Moller-Maersk, and pharmaceutical giant Merck.
The virus also hit Ukraine's Chernobyl power plant, site of the world's worst nuclear accident, forcing it into manual operation.
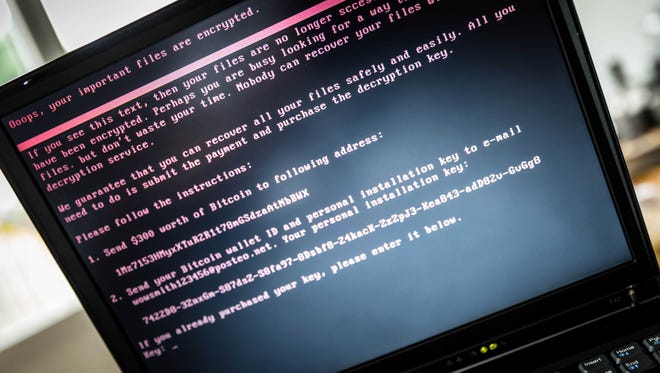
The attack included a text note seeking $300 worth of bitcoin to access files. However, German email company Posteo blocked the email address the Petya perpetrators were using to confirm ransom payments. As of Wednesday afternoon, the attackers have received 45 payments, totaling just over $10,000.
The Peyta ransomware attack follows May's massive Wannacry attack impacting businesses, hospitals, and organizations worldwide. In both cases, hackers demanded a payment in order to unlock encrypted files.
Petya has spread more slowly than WannaCry, which struck more than 150 countries, but it does not include a "kill switch" that undid WannaCry. Experts are still searching for a way to stop Petya.
A researcher from the Boston Cybersecurity firm Cybereason found a temporary fix, or a "vaccine" that prevents further infection. But it is not a universal kill switch that shuts down the entire attack completely and remotely, as was the case with WannaCry.
Both WannaCry and Petya spread by taking advantage of a vulnerability in older Windows systems called EternalBlue, security researchers say. This exploit is believed to have been developed by the National Security Agency and leaked online in April by a group called the Shadow Brokers.
Micorsoft released a patch or a way to fix the vulnerability in March, but many companies still didn't update their systems — even after WannaCry.
But even if companies patched their systems, Petya spreads using more than the EternalBlue exploit, so even if systems fixed the vulnerability, they could still be targets, said Erik Rasmussen, the North America leader of consulting firm Kroll’s cyber practice.
"If a large multinational company has a robust security plan, but has some outlying locations that does not have the updates or the patches, then the entire network could be infected," Rasmussen said.
As to who did it and why: One cybersecurity researcher said the structure of the code indicates the attackers' end game may not have been to make money. Rather, Petya seems like it was designed to wipe files and cause massive disruption, said Matthieu Suiche, founder of the cybersecurity firm Comae, in a blog post.
"The fact of pretending to be a ransomware while being in fact a nation state attack — especially since WannaCry proved that widely spread ransomware aren’t financially profitable — is in our opinion a very subtle way from the attacker to control the narrative of the attack," he wrote.
Ukraine's Interior Minister adviser Zoryan Shkyryak accused Russia of being behind the attack, Ukrainian media reported. And some researchers have posited Russia is a likely culprit because Ukraine was targeted.
A Kremlin spokesman denied the charge in a call with reporters on Wednesday, Reuters reported, saying he had no information about the origin of that attack.
Some security researchers urged caution before attributing the attack to Russia.
"This is just too widespread and too messy and too loud to fit a single country's MO for nation-state attacks," Rasmussen said.
Contributing: The Associated Press
Follow Brett Molina on Twitter: @brettmolina23.